What is Network Monitoring System?

Network Monitoring System is the way to control and monitor the Computer networks that are slow and failing their components. In this process network administrator uses tools to monitors continuously on the incoming and outgoing data and if any bad thing happens used tools notifies network administrator (via email, SMS, or any other sources). Network Monitoring belongs to Network management that is very important for the companies.
As the world developing in IT field so the requirement of Network Monitoring is also increasing. This process is very essential in IT field because in it all the networking components like routers, switches, firewalls, servers and VMs monitored for fault or performance and utilize it to continuously maintain and optimize their availability. There are some layer that are known as OSI Seven Layer Model of Network Monitoring. In this model or function the devices use key functions of a network using networking protocols.
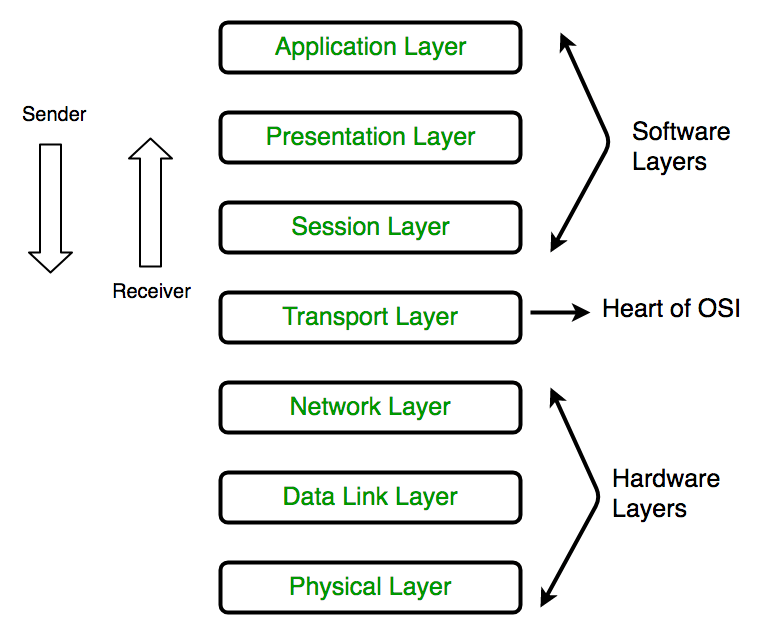
The OSI Seven Layer Model:
Layer1: Physical
Its work to transmit a bit steam over any physical media such as coax or fiber cables.
Layer2: Data Link
Its work is to connecting 2 nodes by detecting their errors at the “Physical Layer”.
Layer3: Network
Its work is to gives routes to data packets to connect 2 nodes via IP address.
Layer4: Transport
Guarantees data move from a source to a destination have across at least one systems.
Layer5: Session
Its Simple work is to control the connection between Computers. It manages, establishes and terminates the connections.
Layer6: Presentation
Its compresses incoming and outgoing data from one format to other (Data encryption, text compression)
Layer7: Application
Connects with programming applications that actualize a conveying part.
In OSI model Data Link, Network, and Application Layers are mostly used for Network monitoring. System Admin or the software that runs for Network Monitoring, uses these layer for detecting the devices, which are connected on the same network and to generate network topology map and monitor the performance.
Network monitoring is such a thing that every company needs or doing. Some companies hire staffs personally for monitoring their Network connectivity but some uses “Manage IT service” Providers. These third party work for those companies and monitor their connectivity. However, with such a huge demand of Network monitoring in market many software vendors developed Network Monitoring Software or Tool. But, choosing right one from the huge range software is little bit difficult. We Suggest For “SolarWinds”. As we work on this platform and give support to many companies and they are completely satisfied with us.
Benefits of SolarWinds:
- Network Management
- Systems Management
- IT Security
- Database Management
- IT Service Management
- Application Management
- Managed Service Providers
Why Network Monitoring is Important?
If you have an IT company or the company that is nothing without their data then it means the Network becomes lifeline of that company. Once your Network Fails or hacked by some dubious hacker groups then work and business gets completely stopped.
If you don’t monitor your Network or don’t have any software or third party support then sometime your network gets sluggish or behave weirdly. And these faulty network devices effects on your work and Application performance.
Cyber Threat Monitoring: Why you need it? What is it?
Cyber Threat Monitoring is term to understand why you need protection from Cyber threats. Cyber threats are those which mainly attacks on your digital data that you store on servers or any electronic device. In Cyber Attack, hackers gain access on your credentials such as banking data, Company details, Employee details, etc… and use these to either blackmail or sell on dark web.
Therefore, any company small or big who uses Internet and stores their data on digital platform needs Cyber Threat Monitoring. It alludes to a sort of arrangement or procedure committed to persistently checking across systems as well as endpoints for indications of security threats, for example, activities at interruptions or data exfiltration. Cyber Threat Monitoring allows administrator to get visibility into the network and the activities of the users that access it. (Today organizations utilize self-employed persons or work from home, freelancers, and staff who utilize their own devices for work, representing extra hazard to the organization’s information and touchy data and driving the requirement for danger observing at endeavors.)
Your Business will always be in danger of Cyber Attacks. Without hesitation, little to medium-sized organizations are bound to endure data breaches, as they frequently have their guards down, having all the target of being obvious objectives for cyber hackers. We always heard about the big tech companies attacked by ransomware or other deadly viruses, there are endless risk that a digital company face on a daily basis. It includes identity-theft, data theft, worms, viruses, Dos (Disk Operating System) attack, web-based attacks and Online fraud. It gives devastating effect on any Company.
Do you Really Need Cyber Threat Monitoring?
Well the answer is not very hard and nothing to think, because no one likes to take risk on their privacy and when it comes to the privacy and data of Company / Business then answer is “Yes”. By using Cyber Threat Monitoring functions you can identify previously undetected Viruses/Worms or outsiders connections that are exploiting your system data and creating a loophole. Mainly by using threat monitoring you will get several Benefits:
- Understand what is happening on network, who is using it, numbers of connected devices, and whether they are at risk or not.
- See how well system utilization lines up with policy needs.
- You will get the vulnerability in Networks, applications, and security firewalls and also how to solve these issues.
- Cyber threat monitoring is a productive procedure to furnish your business with the assets expected to oversee threats and consistence.
- Without cyber threat monitoring, organizations are viewed as a simple, open objective. Notwithstanding business size, cyber crooks will be sufficiently wise to pick the least demanding and most fragile organizations and invade them.